“I sleep better at night knowing that I have LMIT supporting all of our IT needs. They are so attentive and timely, it’s as if we have own in-house IT department. They are not just one of our vendors—they are our partner.”
- Katie Kruft, Executive Vice President - Zislis Group
“Thank you Landmark, you’re always there to help when we need you most!”
Cathy Senior - Butner HOA Services

What is the problem?
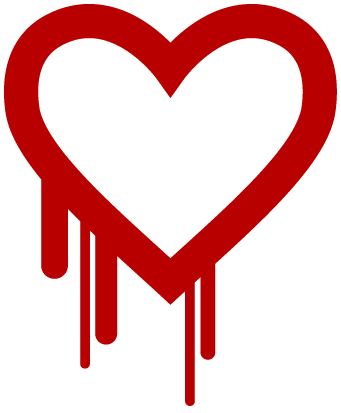
On Monday April 7th, the OpenSSL developers publicly announced a highly critical security flaw that exists in their library. It allows attackers to crack the secure communications of as much as 66% of the web, and steal login-data or impersonate the website. All websites that use the compromised versions of OpenSSL, including big, high traffic websites like Yahoo.com, Flickr, Tumblr and some banks are vulnerable to Heartbleed. This security flaw has existed for 2 years. A list of the top 1000 websites affected can be found here: https://github.com/musalbas/heartbleed-masstest/blob/master/top1000.txt
How might it affect you?
An attacker can steal encryption keys, raw text, emails, passwords, etc. from websites using OpenSSL silently. For example, if you log into a website that has been compromised, it will look exactly how it should with a green secure tick icon in your browser, all while your information is being stolen. The green “secure connection” indicator, saying that you are talking with the right server might not be trustworthy right now.
What can you do?
As a normal user, you can not do much unfortunately. It’s up to the website to patch the site. There’s no way to know you haven’t already had your information stolen.
You can check the websites you log into to see if they are vulnerable to Heartbleed: http://filippo.io/Heartbleed/
You could use this to check HTTPS servers and notify the admins should they be vulnerable. (The :443 at the end of the website means that the HTTPS port is used, and not the normal HTTP port)
Do not log into vulnerable sites until they’re patched by the site’s administrator, once it has been patched you should change your password ASAP. If you log in to change your password before a site has been patched, it could create more problems.
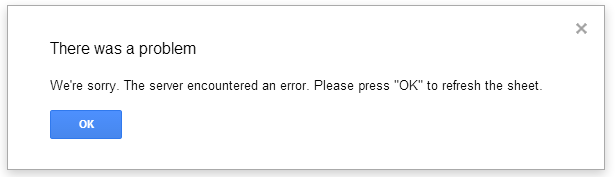
Google drive has been working intermittently for us in the LMIT office and a couple of our clients that are also using Google Apps for business have also reported outages. The Official Google Apps status dashboard is currently showing service disruptions for Google Talk and Google Sheets and Google Hangouts.
To prevent downtime if Drive goes down in the future, it’s a good idea to setup offline access. Google has outlined a guide to walk you through how to do it here.
The remote desktop service LogMeIn gave short notice to its users on Tuesday 1/21/14 notifying them that ‘LogMeIn Free’ will be discontinued. New users can no longer sign up, and existing users are being asked to sign up for a paid tier, which begins at $49/year for two computers.
Users have seven days to make their decision about LogMeIn Pro, with the timer set the next time they log in (and not before). In other words, the 7-day grace period starts when you next login to the LogMeIn service. The company’s other free services, for example Join.me, will continue to be free and operate as before.